What to consider
The automotive industry has produced an explosion in internet connectivity, now commonplace in vehicles this connectivity increases the risk that privacy and safety will be threatened. In 2015, we got a glimpse at what is at stake, when two security researchers hijacked a vehicle over the internet. They were able to turn the steering wheel, briefly disable the brakes, and shut off the engine. The implications of this exercise were clear and troubling at the time. Now with many more cars internet-enabled, the risk of hijacking has exploded and the trend will continue unabated because consumers want the convenience of connectivity. However, every new convenience adds risk, and current security protections generally fall short of countering that risk. Many organizations are pursuing emerging technologies to develop new products, services or ways of doing business. However, companies don’t always consider the emerging cybersecurity threats that could impact these systems after they’re implemented. CloudGRC Inc. can help your organization design and implement strategies with security and compliance requirements from the very start,
Cloud concerns
The automotive industry is under constant pressure to increase productivity, make time-to-market a competitive differentiator, and optimizes their supply chain, distribution, and customer relationships. The cloud enables businesses to streamline operations and better compete at all levels. However, with more and more cloud and web services, it’s important to understand and manage the risks that can come with the cloud. From supplier contracts to business plans to product plans to intellectual property and trade secrets, the unintentional or intentional exposure of data can have a negative impact on your business. Without visibility and control across SaaS, IaaS, and web, manufacturers can’t govern usage to ensure protection of that data. To ensure cloud security in your organization, CloudGRC Inc. empowers you to understand what cloud and web services are in use and how they are being used, enforce access controls, protect sensitive data, and restrict risky activities.
Target-rich environment
Nearly every car for sale today has a telematics unit and other components that provide a connection to the outside world. Connected car components make it possible to remotely attack infotainment, diagnostic functions, or even core features like the engine control unit. New cars have been equipped to provide real-time status information and possess the ability to control aspects of the car remotely. These features rely on Bluetooth and Wi-Fi and cellular radio signals to communicate, while their under lying computers are often based on platforms with both software and hardware vulnerabilities. They connect with the infotainment systems on car dashboards, which closely interact with travelers in the car through their mobile phone devices. As a connected device the vehicle is vulnerable to attack.
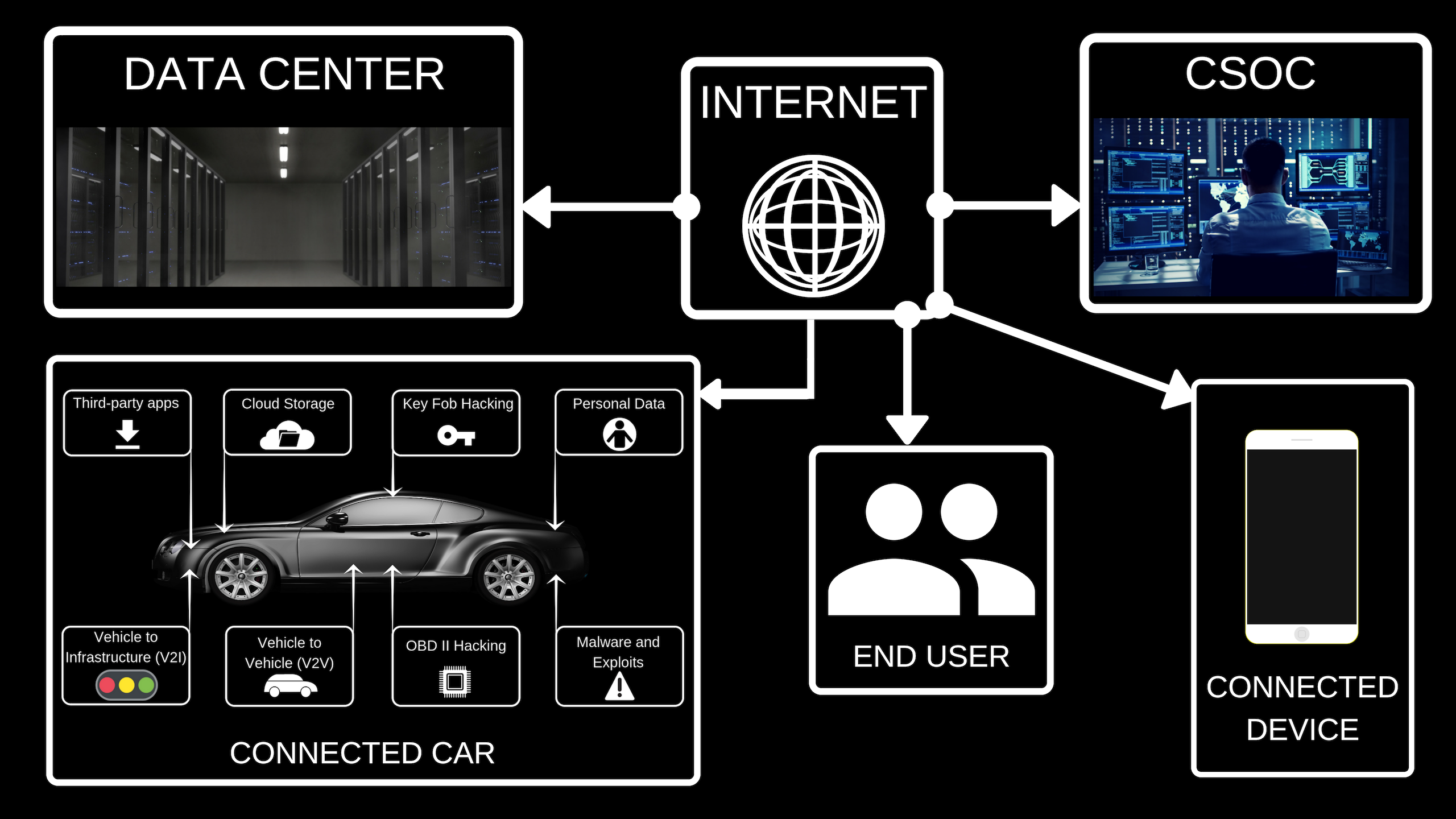
Automobile safety has to be supported by an enterprise-wide program that coordinates cyber defenses across all production platforms, internal operations, and supply chains. A weakness in one area can infect the rest of the enterprise and result in, for example, car failure, factory slowdowns, the hacking of customer data, or the theft of intellectual property. There are several obvious entry points for hackers, including vehicles, factory machines and supply chains. CloudGRC Inc. develops a holistic approach to fight cyberattacks that includes prevention, detection, and reaction as well as feedback mechanisms.


